It seems every week we hear of another Ransomware attack, which are most likely the tip of the iceberg. Below the surface is a slew of attacks that we do not hear about as businesses are naturally reluctant to publicize these. The bad guys are getting more sophisticated and are using social media reconnaissance not only for phishing exploits to get in, but to also understand the company’s revenue pattern, both size and timing. For example, with that research, they can easily wait until the last two weeks of the quarter and then demand 1/2 the expected revenue, knowing that there is not enough time for the company to restore the necessary.
Mid-size companies with smaller IT network security staffs are particularly vulnerable, however, recent headlines prove that even the largest companies are vulnerable to failing to apply security patches in time. Revenue loss is not the only issue with these attacks, negative publicity and the resulting customer distrust can have a longer and more devastating impact.
So what can IT organizations do to turn the tide? Here are three ideas:
- Practice Good Security Hygiene. Just like taking a shower and brushing our teeth become part of our daily routine, keeping an eye out for phishing attempts should be a part of employees’ daily routine. Educating end-users to be more aware of these types of social engineering tactics and to take a little extra time before replying to emails to ask themselves if this MIGHT be an exploit can act as a first line of defense. Many times, it is the simple things that get easily overlooked, like one extra character in the middle of the email address, that can be a tripwire to a breach.
- Identify the business-critical production systems. Willie Sutton, the famous bank robber, said that the reason he robs banks is, “because that is where the money is.” Spending time to think like Willie Sutton can help identify where attacks will try to get the most return on their ransomware attack.
- Implement an Air Gap. This idea offers the best potential “Last Line of Defense.” Dell EMC currently offers an innovative approach call Isolated Recovery. It works like this:
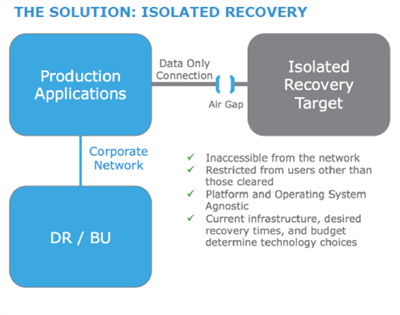
If you would like to have a discussion on how Sanity Solutions can help architect a data protection and recovery solution for your organization, contact us at in**@sa*************.com.

